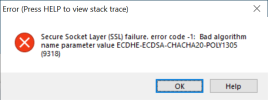
/*------------------------------------------------------------------------
File : TLSConnect.p
Purpose :
Syntax :
Description :
Author(s) : James Bowen
Created : Wed Nov 22 16:28:37 NZDT 2023
Notes :
----------------------------------------------------------------------*/
/* *************************** Definitions ************************** */
block-level on error undo, throw.
/* ******************** Preprocessor Definitions ******************** */
/* *************************** Main Block *************************** */
using OpenEdge.Net.HTTP.IHttpRequest.
using OpenEdge.Net.HTTP.IHttpResponse.
using OpenEdge.Net.HTTP.ClientBuilder.
using OpenEdge.Net.HTTP.RequestBuilder.
using OpenEdge.Net.HTTP.IHttpClientLibrary.
using OpenEdge.Net.HTTP.Lib.ClientLibraryBuilder from propath.
define variable oRequest as IHttpRequest no-undo.
define variable oResponse as IHttpResponse no-undo.
define variable oLib as IHttpClientLibrary no-undo.
define variable cSSLProtocols as character extent 2 no-undo.
define variable cCiphers as character extent no-undo .
define variable cAllowedCiphers as character no-undo.
define variable inArrayIndex as integer no-undo.
assign
cSSLProtocols[1] = "TLSv1.3":U
cSSLProtocols[2] = "TLSv1.2":U.
Assign
//cAllowedCiphers = "TLS13-AES-256-GCM-SHA384, TLS13-AES-128-GCM-SHA256, TLS13-CHACHA20-POLY1305-SHA256, ECDH-ECDSA-AES256-GCM-SHA384, ECDH-ECDSA-AES128-GCM-SHA256, ECDHE-ECDSA-CHACHA20-POLY1305"
//cAllowedCiphers = "ECDH-ECDSA-AES256-GCM-SHA384, ECDH-ECDSA-AES128-GCM-SHA256, ECDHE-ECDSA-CHACHA20-POLY1305"
cAllowedCiphers = "ECDH-ECDSA-AES256-GCM-SHA384, ECDH-ECDSA-AES128-GCM-SHA256":U
.
extent(cCiphers) = num-entries(cAllowedCiphers).
do inArrayIndex = 1 to extent(cCiphers):
cCiphers[inArrayIndex] = trim( entry(inArrayIndex, cAllowedCiphers ) ).
end.
.
oRequest = RequestBuilder:Get('https://services.ird.govt.nz/gateway2/gws/returns/?WSDL'):Request.
oLib = ClientLibraryBuilder:Build()
:SetSslCiphers(cCiphers)
:SetSSLProtocols(cSSLProtocols)
:Library.
oResponse = ClientBuilder:Build()
:UsingLibrary(oLib)
:Client
:Execute(oRequest).
message
substitute("&1 &2",oResponse:StatusCode, oResponse:StatusReason) skip
oResponse:GetHeader("content-length":U) skip
oResponse:GetHeader("content-type":U) skip
oResponse:GetHeader("Date":U) skip
view-as alert-box info.
finally:
if valid-object(oResponse) then
delete object oResponse.
if valid-object(oRequest) then
delete object oRequest.
end finally.