KMoody
Member
Progress: 10.2b SP7
OpenEdge Architect: 3.4.2.R342_v20090122-9I96EiWElHi8lheoJKJIvhM3JfVsYbRrgVIWL
OpenEdge OS: Windows 7 Professional 2009 SP1
I want to assign permissions based on which group(s) a user belongs to rather than using individual user names.
OpenEdge Architect: 3.4.2.R342_v20090122-9I96EiWElHi8lheoJKJIvhM3JfVsYbRrgVIWL
OpenEdge OS: Windows 7 Professional 2009 SP1
I want to assign permissions based on which group(s) a user belongs to rather than using individual user names.
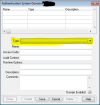
- In my permissions table, could I use groups instead of names and run something like this before running a program?:
Code:
permission:
Activity | Can-Run
-------------------------
custedit | management,hr,it
ordedit | management,hr,it
itemedit | management,sales,it
reports | management,inv,sales,it
USER-GROUPS
USER-GROUPS-ID| MEMBER-ID
-------------------------
management | staceyc
management | jsmith
hr | hnobody
FUNCTION hasPermission RETURNS LOGICAL (INPUT procedureName AS CHAR):
FIND permission WHERE Activity = procedureName.
FOR EACH USER-GROUPS WHERE USER-GROUPS.MEMBER-ID = userid NO-LOCK:
IF CAN-DO (permission.Can-Run, USER-GROUPS.USER-GROUPS-ID ) THEN DO:
DISPLAY "You have permission!".
RETURN TRUE.
END.
END.
DISPLAY "You do NOT have permission!".
RETURN FALSE.
END FUNCTION.- In the Data Administration tool, how can I edit Data Security using groups instead of user names? If this isn't possible, then can I do this programmatically?