GregTomkins
Active Member
10.2B05, HP-UX
I have code that uses ABL sockets to communicate with a web server. It's been running for weeks without incident. Today, we installed it on a different server. Suddenly, it fails 100% of the time (on that server only).
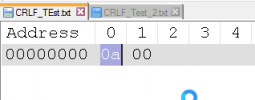
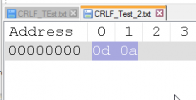
The symptom is that following a seemingly normal connection, GET-BYTES-AVAILABLE (which normally returns sensible positive values) consistently returns '-276921288'.
Progress KB has nothing of value that I could find. The Internet says that negative values in TCP reply lengths are associated with a reply that isn't properly delimited. But I am pretty sure (I don't have access to it) the remote host is responding correctly since it correctly responds to requests from many other servers.
Same OS and Progress version in all cases
No external configuration (that I can see) that could vary between servers
I cannot deduce any significance to the value 276921288
I don't have access to curl, WireShark, tcpdump, nettl etc. on this area of our network
The only difference (that I can think of) that I can't be 100% sure about is the surrounding network environment as it is managed by people that I have no access to. Anyway, if there was a proxy screwing things up, or similar, I would expect it to outright refuse the connection.
Any ideas?
I have code that uses ABL sockets to communicate with a web server. It's been running for weeks without incident. Today, we installed it on a different server. Suddenly, it fails 100% of the time (on that server only).
The symptom is that following a seemingly normal connection, GET-BYTES-AVAILABLE (which normally returns sensible positive values) consistently returns '-276921288'.
Progress KB has nothing of value that I could find. The Internet says that negative values in TCP reply lengths are associated with a reply that isn't properly delimited. But I am pretty sure (I don't have access to it) the remote host is responding correctly since it correctly responds to requests from many other servers.
Same OS and Progress version in all cases
No external configuration (that I can see) that could vary between servers
I cannot deduce any significance to the value 276921288
I don't have access to curl, WireShark, tcpdump, nettl etc. on this area of our network
The only difference (that I can think of) that I can't be 100% sure about is the surrounding network environment as it is managed by people that I have no access to. Anyway, if there was a proxy screwing things up, or similar, I would expect it to outright refuse the connection.
Any ideas?