S
Susan Lamatrice
Guest
Learn more about enterprise security, encompassing authentication, encrypted communication, authorization and data auditing.
Our recent webinar, Enterprise Security in Data Access, gives a detailed look at security implementations in the data access landscape. Security is far more than the user id and password logon box that we’re all familiar with. In an enterprise landscape, security encompasses authentication, encrypted communication, authorization, and data auditing. Each of these areas has a breadth of technologies and challenges to confront.
For more on this topic, let’s meet Brian Derwart. Brian is a Product Owner in Research and Development at Progress. He’s been working on DataDirect products since 1999. Brian has deep expertise in driver wire protocol and network communication for on premises and cloud-based relational and NoSQL databases.
Let’s discuss some questions that Brian addressed on our recent webinar in relation to the technologies involved in authentication, encryption, authorization, and data auditing.
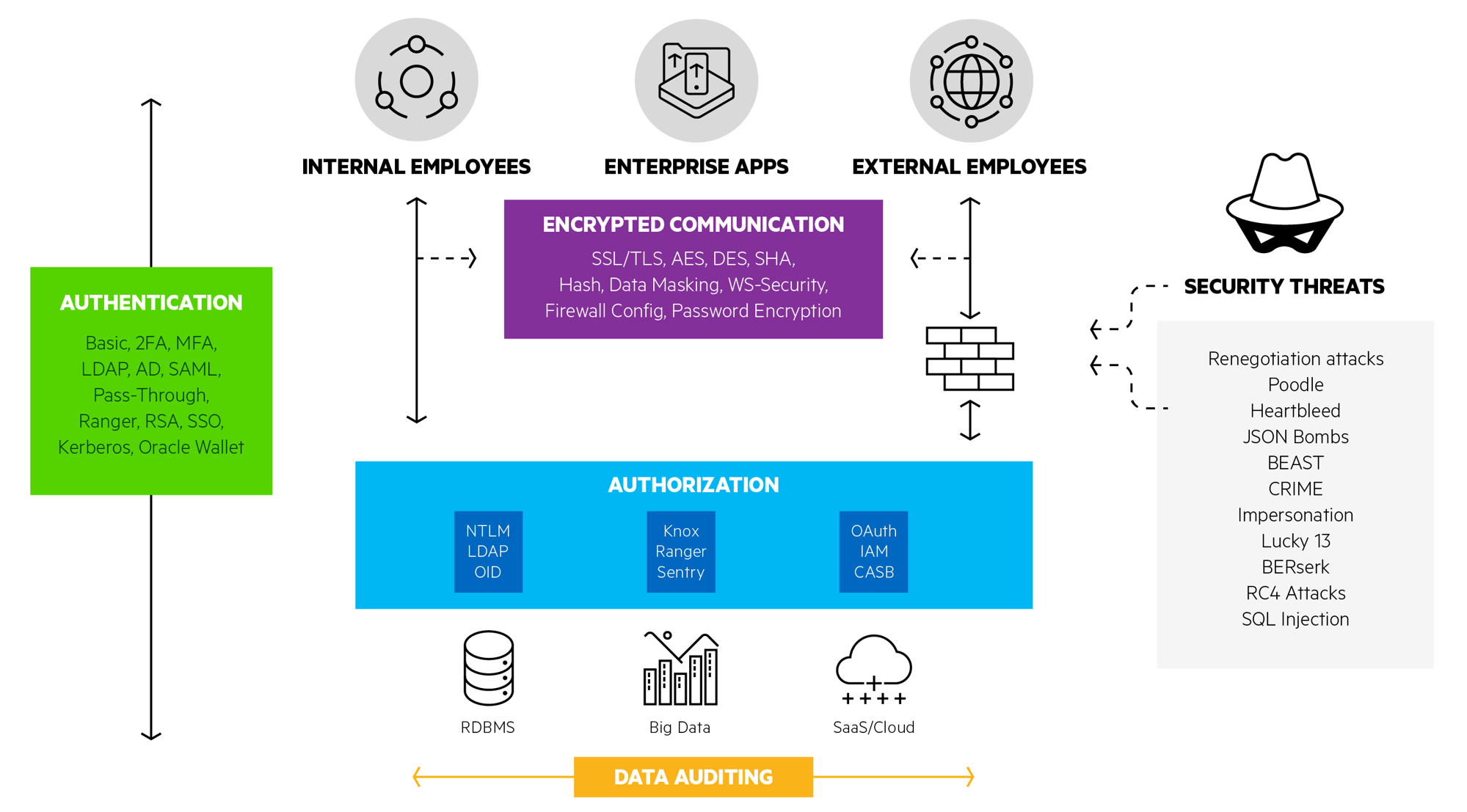
Interview with Brian Derwart
Thanks for joining us Brian. There’s a lot going on in the graphic above (readers: click to enlarge), so let’s start with Authentication. What’s the best choice for user authentication?
Brian Derwart: When it comes to verifying user identity, you first have to consider your requirements. Sending passwords over the network might be acceptable in a development environment behind a firewall, but not likely secure enough in a production or cloud-based data access environment. You may wish to access cloud-based services where your identity is verified using two or more methods, called two-factor or multi-factor authentication. A more secure alternative is to use Kerberos. Kerberos is a computer network authentication protocol that uses tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Windows Active Directory uses Kerberos as its default authentication mechanism, and while Active Directory simplifies this ticket-granting process, there is additional overhead to managing user and service tickets in app and web server environments where you have multi-tiers. There are numerous implementation choices to make within authentication.
How is authorization different from authentication?
Brian Derwart: Authentication is knowing who the user is, authorization is what that user is allowed to do once they’re logged into the system. We have service level authorization, where the database itself is the service, and permissions can be set with an active directory or on LDAP as to whether users have access to that database service. Within the database, we can set user permissions or role-based permissions. These permissions can be at the database level, table level, column level, and can enable read-write access versus read-only or metadata only authorization.
On the webinar we go a bit further using OAuth as an example. OAuth is an authorization protocol rather than an authentication protocol. The OAuth process does include several kinds of authentication but the existence of these authentication events within the OAuth protocol does not translate to the OAuth protocol itself being able to reliably convey authentication. In order to provide authentication on top of this authorization provided by OAuth, OpenID allows you to use an existing account to sign into multiple websites without needing to create new passwords.
How does data masking come into play?
Brian Derwart: Data masking, or redaction, is when sensitive data transmitted back to the user is masked out. So, for example, even if your users can query data that includes a Social Security number, you typically don’t want to communicate full social security numbers back to all your users, so perhaps you redact all but the last four digits in that scenario.
Is encryption strictly for network security?
Brian Derwart: Encryption is critical both as data is moved over a network and when data is at rest on disk. The most frequent technologies we see on the network are SSL and TLS encryption which negotiate a cipher to determine how data gets encrypted. Another way to verify that the data was received without man-in-the-middle attack is through a hash, so the data itself is hashed, and that data integrity is verified at the client level by verifying the hash matches a hash that’s generated on the client side. Data-at-rest encryption doesn’t get as much attention, but it’s more important than you may think. Even when data is stored on disk in the database, if the data itself is encrypted and anyone accesses that host machine, they only ever see encrypted data and there’s really no way to steal anything since the encryption key is not stored in the database.
Does SSL/TLS encryption add performance overhead?
Brian Derwart: With network traffic security concerns, LDAP communication can be encrypted using SSL or TLS, and while encryption usually adds performance overhead, connections from clients to the LDAP server are persistent so that once the authentication step is complete, the rest of the communication is actually fairly cheap. LDAP network communication is lightweight in terms of the binary ASN.1 encoded packets, which means that they are compact and easy to parse. Windows Active Directory and Oracle Internet Directory both use LDAP implementations for managing user authentication authorization.
What’s new in the realm of Data Auditing?
Brian Derwart: Really the big feature this year is detecting threats as they occur, as opposed to after the fact. Databases are adding this concept of smart technologies where they look at trends in data access, such as where the user’s logging in from, or what sort of data they’re requesting, and try to develop algorithms to determine whether there are differences based on this user’s typical behavior. If it’s construed as an attack, the database can be coded to shut that user down and stop the attack as it’s happening.
Brian, thanks so much for your time. For more comprehensive detail on Enterprise Data Security including all of the topics discussed above, watch the full webinar.
View Webinar
Continue reading...
Our recent webinar, Enterprise Security in Data Access, gives a detailed look at security implementations in the data access landscape. Security is far more than the user id and password logon box that we’re all familiar with. In an enterprise landscape, security encompasses authentication, encrypted communication, authorization, and data auditing. Each of these areas has a breadth of technologies and challenges to confront.
For more on this topic, let’s meet Brian Derwart. Brian is a Product Owner in Research and Development at Progress. He’s been working on DataDirect products since 1999. Brian has deep expertise in driver wire protocol and network communication for on premises and cloud-based relational and NoSQL databases.
Let’s discuss some questions that Brian addressed on our recent webinar in relation to the technologies involved in authentication, encryption, authorization, and data auditing.

Interview with Brian Derwart
Thanks for joining us Brian. There’s a lot going on in the graphic above (readers: click to enlarge), so let’s start with Authentication. What’s the best choice for user authentication?
Brian Derwart: When it comes to verifying user identity, you first have to consider your requirements. Sending passwords over the network might be acceptable in a development environment behind a firewall, but not likely secure enough in a production or cloud-based data access environment. You may wish to access cloud-based services where your identity is verified using two or more methods, called two-factor or multi-factor authentication. A more secure alternative is to use Kerberos. Kerberos is a computer network authentication protocol that uses tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Windows Active Directory uses Kerberos as its default authentication mechanism, and while Active Directory simplifies this ticket-granting process, there is additional overhead to managing user and service tickets in app and web server environments where you have multi-tiers. There are numerous implementation choices to make within authentication.
How is authorization different from authentication?
Brian Derwart: Authentication is knowing who the user is, authorization is what that user is allowed to do once they’re logged into the system. We have service level authorization, where the database itself is the service, and permissions can be set with an active directory or on LDAP as to whether users have access to that database service. Within the database, we can set user permissions or role-based permissions. These permissions can be at the database level, table level, column level, and can enable read-write access versus read-only or metadata only authorization.
On the webinar we go a bit further using OAuth as an example. OAuth is an authorization protocol rather than an authentication protocol. The OAuth process does include several kinds of authentication but the existence of these authentication events within the OAuth protocol does not translate to the OAuth protocol itself being able to reliably convey authentication. In order to provide authentication on top of this authorization provided by OAuth, OpenID allows you to use an existing account to sign into multiple websites without needing to create new passwords.
How does data masking come into play?
Brian Derwart: Data masking, or redaction, is when sensitive data transmitted back to the user is masked out. So, for example, even if your users can query data that includes a Social Security number, you typically don’t want to communicate full social security numbers back to all your users, so perhaps you redact all but the last four digits in that scenario.
Is encryption strictly for network security?
Brian Derwart: Encryption is critical both as data is moved over a network and when data is at rest on disk. The most frequent technologies we see on the network are SSL and TLS encryption which negotiate a cipher to determine how data gets encrypted. Another way to verify that the data was received without man-in-the-middle attack is through a hash, so the data itself is hashed, and that data integrity is verified at the client level by verifying the hash matches a hash that’s generated on the client side. Data-at-rest encryption doesn’t get as much attention, but it’s more important than you may think. Even when data is stored on disk in the database, if the data itself is encrypted and anyone accesses that host machine, they only ever see encrypted data and there’s really no way to steal anything since the encryption key is not stored in the database.
Does SSL/TLS encryption add performance overhead?
Brian Derwart: With network traffic security concerns, LDAP communication can be encrypted using SSL or TLS, and while encryption usually adds performance overhead, connections from clients to the LDAP server are persistent so that once the authentication step is complete, the rest of the communication is actually fairly cheap. LDAP network communication is lightweight in terms of the binary ASN.1 encoded packets, which means that they are compact and easy to parse. Windows Active Directory and Oracle Internet Directory both use LDAP implementations for managing user authentication authorization.
What’s new in the realm of Data Auditing?
Brian Derwart: Really the big feature this year is detecting threats as they occur, as opposed to after the fact. Databases are adding this concept of smart technologies where they look at trends in data access, such as where the user’s logging in from, or what sort of data they’re requesting, and try to develop algorithms to determine whether there are differences based on this user’s typical behavior. If it’s construed as an attack, the database can be coded to shut that user down and stop the attack as it’s happening.
Brian, thanks so much for your time. For more comprehensive detail on Enterprise Data Security including all of the topics discussed above, watch the full webinar.
View Webinar
Continue reading...
