Cecil
19+ years progress programming and still learning.
I had a situation where the DLC cert folder needed to be updated with a missing CA root certificate.
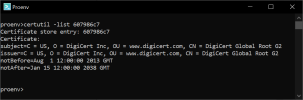
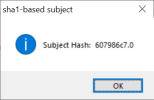
OpenEdge raised an error about certificate 6079867.0 was missing.
I managed to get the certificate root file and import it successfully, but I'm unsure how the hash is calculated.
From what I have found on the internet, the hash is calculated by SHA1 on the "subject issuer" and then taking the first 4 bytes and hex-encoding the result.
However, no matter what I try, I'm just unable to calculate the same hash that OpenSSL generates.
Objective:
I want to test to see if a certificate exists in the %DLC%/cert folder and to do that I need to make sure I can calculate the hash.
I can't assume that OpenSSL utility is installed on a desktop PC, so using OpenSSL is not an option to calculate the hash for me.
Question:
In the ABL how do I calculate the hash of a certificate?
OpenEdge raised an error about certificate 6079867.0 was missing.
I managed to get the certificate root file and import it successfully, but I'm unsure how the hash is calculated.
From what I have found on the internet, the hash is calculated by SHA1 on the "subject issuer" and then taking the first 4 bytes and hex-encoding the result.
However, no matter what I try, I'm just unable to calculate the same hash that OpenSSL generates.
$ openssl x509 -in "DigiCert Global Root G2.crt" -hash -noout
607986c7
Objective:
I want to test to see if a certificate exists in the %DLC%/cert folder and to do that I need to make sure I can calculate the hash.
I can't assume that OpenSSL utility is installed on a desktop PC, so using OpenSSL is not an option to calculate the hash for me.
Question:
In the ABL how do I calculate the hash of a certificate?
Last edited: